What do VPN services always say? “Being on the internet means you’re under threat, hackers are out to get you and steal your private data, we can help.” I’ve worked at some VPN companies and even written taglines like that. While there are places that VPNs can help, it’s not as clear cut as the marketing seems.
Here I’ll dive into how, and where, VPNs are actually useful.
Note: When I say “VPNs” I’m talking about VPN services that advertise to you and me. Of course, VPN software is useful in corporate settings and lots of other areas, but this page is about consumer VPN services.
Who am I?
Hi there! I’m Daniel, affectionately known as ‘doaks’ to my VPN friends. Do I really know what I’m talking about? Well I’ve worked at a couple of VPN companies, where I’ve:
- Been a senior technical customer support manager. I would help our customers, and tech support staff, figure out why their VPN wasn’t working, comb through OpenVPN logs to find issues, and answer all kinds of technical questions about VPNs.
- Helped train up our customer service and QA staff. This involved making docs that helped explain how VPNs worked to our support team, videos explaining our software, and more.
- Been the Head of Quality Assurance for a large VPN company. This meant that my team and I would check every VPN software update before it went out, and would also investigate new security-critical bugs that got reported.
- Written public blog posts explaining VPNs and networks.
Basically I’ve spent most of my time at VPN companies understanding and explaining all this, and am pretty good at it. This is the kind of content I’d write for my workmates every day!
How does a VPN work?
Let’s quickly explain how VPN services work.
By default, when your device talks to the internet, it just… talks to the internet! All web services see and communicate with your device’s public IP address.
When using a VPN your device only talks to the VPN server – all of your web traffic is sent through that server and then out to the internet. All the web services you use see and communicate with the VPN server’s IP address instead of yours.
Theoretically, this does a few things:
- Your internet traffic is combined with the internet traffic of a lot of other people, to make it harder for web services to know who is really using that VPN server.
- Nobody sitting between your device and the VPN server can figure out what you’re sending or receiving. All they see is a single connection to the VPN server, without a way to work out what happens from there.
There can also be other features like: double-hop where the traffic will be forwarded through one VPN server and then another, split tunnelling where some traffic will go through the VPN server and some won’t, but the above is the basic case.
VPN companies are all about trust
Yes, VPN software can give you a lot of technical protection and features. But would you use that software if you didn’t trust the company providing it? Of course not!
And would you waste the bandwidth and speed that it takes to run VPN software if you completely trusted your ISP, government, and whoever else could access your network? Nope.
VPN companies want you to trust their system more than you trust all of those other groups. That trust can be built by providing good service (making it fast, not going down, apps work well), good support, proving their claims, and making other tools that help you stay protected.
Once you understand that being trusted is critical, sometimes even more important than actually improving your security, the marketing makes a lot more sense.
However…
Accessing geo-locked content and allowing all kinds of web traffic are both super important as well, and for an amount of users may even be more important than security. I’ve always been focused on the privacy and security side though, so that’s what this article will look at.
Understanding threats
If you’re thinking about a VPN for security purposes, start by thinking about your threat model.
Your threat model is… what do you consider threats that you need to protect against? What are probable threats for you, what do you need to protect yourself against, etc? Once you have your threat model, you can dive into how, and whether, a VPN service will be useful for you.
Here are some potential threats:
- Being on free or shared wifi.
- People hacking your web accounts.
- People getting into your computer.
- Getting sent copyright infringement notices and having your internet cut off.
- Others seeing your internet traffic / the websites and pages you visit.
- Others seeing your IP address.
- Your internet being ‘exposed’ and ‘not protected’.
Let’s dive into some specifics on each of these, and why they may or may not be issues.
Being on free or shared wifi
There are a decent number of legitimate risks here. Mostly man-in-the-middle attacks where either: a villian connects to the same wifi and is able to see your internet traffic, or they trick your computer into connecting to a wifi network they control instead of the real one.
Why’s this a risk?
They can do whatever they want with your connection: Snoop on what you’re sending to extract passwords, change the responses to send you different data, or whatever else they want. And even if they don’t see the traffic, they may still be able to see which sites you’re accessing by looking at your DNS requests (the system that turns website names into addresses your computer can contact, see more info here).
Why’s this not a risk?
There’s been a big push to encrypt the web since this was a headline risk. Since a good amount of the web is now encrypted-only and there are technologies like HSTS which tell browsers to only use HTTPS if you have already visited the webpage, and preload lists that help cover gaps, these villains aren’t going to get as much useful info out of your web traffic, even if they do take it over.
This can definitely happen today, and a VPN protects you by making sure that your computer only connects to the VPN company’s servers, and does so in an encrypted way. If you trust the VPN service, it could be worth it.

People hacking your web account / your computer
Hackers want to steal your data, oh no! This is one of the biggest risks that many VPN services claim to protect against, but is it accurate?
Why’s this a risk?
People click on bad links and give up info all the time. As well as that, people can e.g. receive ‘game’ links through Discord or bad email attachments, run them, and get hacked. In addition, web services are getting hacked and peoples details are released all the time, constantly.
Why’s this not a risk?
On the web account side, this isn’t an issue for a VPN to solve because, well, the VPN isn’t anywhere near the threat. If people are hacking into the web service you’re using (say, they’re hacking Facebook), you using a VPN could prevent… your IP address from being leaked from Facebook’s database, maybe? But Facebook would still have your name, password, card details, and whatever else was stored on their site.
If the villain is hacking into your computer, then you need to keep in mind that a VPN isn’t a firewall or virus protection. Your computer is still online and accessing the internet, and you can still click on a virus and start running it. Your computer can still be infected and then remote-controlled by a villain – without the VPN saving you.
I’m not convinced that this is a risk VPN services with regular ole’ VPN software can solve. This is one of those ‘trust’ things – it’s easy to point at the hacks, say their VPN software sits between you and the internet, and say because of that they can stop it from happening. Use antivirus software and a password manager and keep them updated, that’s what will help here.

Getting sent copyright infringement notices and having your internet cut off
Yeah, this happens a fair bit. It sucks, and it’s one of the things that a VPN is really useful for.
Why’s this a risk?
‘Copyright protection’ companies scan torrents and other download services, collect the IP addresses of everyone downloading certain files, and then sends copyright infringement notices to the ISPs. It’s pretty simple to do, just click in the ‘peers’ list when you’re torrenting a Linux ISO the next time and you can see everyone’s IP addresses.
Why’s this not a risk?
It’s only an issue is you download things using file-sharing services. And nobody would ever do that, right? 🤔 🏴☠️ 📼
If you set it up properly, a VPN will definitely help here. I repeat: IF YOU SET IT UP PROPERLY.
Use this site, and especially the Torrent leak detection, to make sure that your VPN is set up and working as expected: https://ipleak.net/. Generally, all the addresses you see should match the one that your VPN software tells you you’re using.
Others seeing your internet traffic / the websites and pages you visit
This is an important one, both in the western world and elsewhere. And it’s one of the main risks that I’d think about and test for daily when doing QA runs of our VPN software.
Why’s this a risk?
This is a risk for everyday people. Depending on where you live, your country may have mandatory data retention laws (see Australia, NZ, etc), or you may simply be searching for things that are illegal where you live. For example, maybe you’re a parent in Florida searching for healthcare advice for your trans child, or maybe you need to see abortion advice in one of the US states that has callously outlawed it. Maybe you’re inside China and want to see past the Great Firewall.
(By the way, ‘Metadata collection’ involves a lot of data. Where you visit, the size of the content, how long connections last, and a whole suite of other information. Just because they may not be able to see the page content or the the data you send, doesn’t mean the data isn’t valuable or useful. Rant over.)
This is also an issue for journalists and their sources. It’s pretty obvious why. (When unfriendly countries see what they search and expose, it can result in harsh backlash.)
Why’s this not a risk?
For a lot of people, this isn’t something that they would usually care about. I doubt that grandpa cares very much that the government could see what he’s buying on Facebook Marketplace, you know? The analogy I tended to use is “would you go to the bathroom with your front door open?”, which gets people thinking, but in terms of the web it’s debatable whether that’s as relevant of an analogy for raw internet traffic today. Given how much HTTPS and secure-first services are out there, the amount of information that you can get from internet traffic is… potentially reduced. You could also argue that there’s more going on online every day, so it’s debatable.
If you really are being hunted or spied on by a major intelligence organisation or someone similar, it’s likely that they can get you on something other than your internet traffic, and using a simple VPN service probably won’t be enough to save you.
For me, this is one of the most important things that VPN services can affect. Think about whether or not this is a risk you care about, but also keep in mind… if you do use a VPN service then all of your internet traffic goes to them instead.
Do you trust the VPN service you’ve chosen with all of this info? Is there any possibility that they’d process and sell the data to a marketing firm, or work with the above groups to provide them with your internet traffic? When you use a VPN you’re very explicitly saying that you trust that VPN company much more than you trust any other groups with your raw internet traffic, so have a good think about it.
Others seeing your IP address
This could be an issue, or it may not be. Let’s dig into it to find out.
Why’s this a risk?
If you’re playing games or accessing services where other users can see your IP address directly, those other users could DDoS your connection or do other kinds of things. For example, if you’re a streamer then others having your IP address could be really bad. They could DDoS you meaning your stream goes down, or other kinds of disruption. Since your IP address can sometimes give your location in more detail than just the city you live in, there’s also the possibility that it could help bad actors find where you live.
The websites and services you access can see your IP address whenever you visit or connect to them. This could be bad if, for example, those sites are honeypots (sites setup by villians to try to trick you), because then they would have your IP address!
Why’s this not a risk?
For most of us, sites and other users having our IP address isn’t the end of the world. Most people that we meet or play with aren’t going to bother with the effort to find our IP address even if they had the ability to do so.
With websites and services, if you’ve signed up for an account then you’re already providing them with more info than your IP address could give them. The most scary thing they can do with it is probably show where in the world you are and what ISP you use.
This one’s a risk for certain people, but less of a concern than the ads would have you believe. Since we have firewalls (i.e. most computers aren’t connected directly to a public internet address and won’t just accept any inbound connection) it’s less of an exploitable issue tech-wise and more of a general privacy thing to consider.
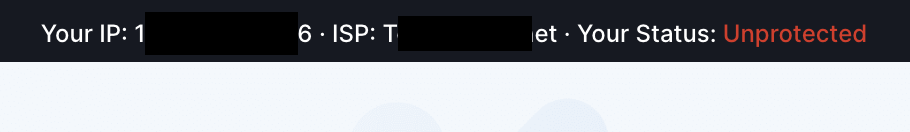
Your internet is ‘exposed’ and ‘not protected’
This is one of the other common things that VPN services talk about. Using a VPN makes your connection protected and iron-clad and gives you a pretty little lock symbol, but not using a VPN means that your internet is bad and sad and at risk.
This is entirely marketing and trust. You activate the VPN, and then either in the VPN software itself or on the VPN service’s site you see that ‘not protected’ red text turn green and now say ‘protected’. It’s a fancy way to show whether or not you’re using that provider’s VPN service (notice, even if you’re using a competitor’s VPN then it’ll still say ‘unprotected’).
Being protected or not protected online involves a lot more than whether or not you’re using a VPN. These services and software can protect against a number of risks, but “your internet service being exposed and not protected” isn’t one to worry about. The firewall built into your ISP modem or phone already solved that.
So should I use a VPN?
A VPN service would be useful to you if it prevents one of the above risks, and/or gives you another feature like accessing geo-locked content. Look at the above examples, think about your threat model in general, and whether or not a VPN will improve your security should become obvious. The marketing says that everyone should use a VPN at all times to keep protected… but have a good think about it.
Who knows, by thinking about the threats you face you might even come up with solutions you haven’t considered yet!
Note, if you enjoyed this explanation and want to learn more about computer networking, check out my free networking guide, no sign-ups or emails necessary – it goes through a set of topics that are vital to understanding the technical side of the internet and how devices communicate. And if you have any examples I didn’t cover or questions/comments, please send me an email.
All the best, and happy internet-ing!